
How to protect your website & company from a cyber attack?
In light of the significant increase in the frequency and magnitude of cyberattacks in 2017, businesses are increasingly concerned about the protection of their websites security and their sensitive data.
Indeed, the year has already been marked by the propagation of several large-scale malware.
On June 27, major companies, airports, hospitals, academic institutions, metro systems and government departments were hit by a massive cyberattack, dubbed NotPetya (sometimes Petya or GoldenEye), that began to spread around the world.
This ransomware-type cyberattack, comes shortly after WannaCry, which had affected more than 300,000 computers across 150 countries last month.
The organizations most affected by the new NotPetya virus are located in Russia and Ukraine, but also in the United Kingdom, Germany, France, Italy, the United States and Poland. French companies such as Saint-Gobain, Auchan and SNCF have reported being infected.
These unprecedented cyberattacks highlight the cybersecurity challenges organizations face.
What is malware?
Malware is a type of computer program designed to harm a computer. Malware can steal, damage or destroy sensitive information from your computer, spread to other systems or servers connected to the network, or even send fake emails from your email account without your knowledge.
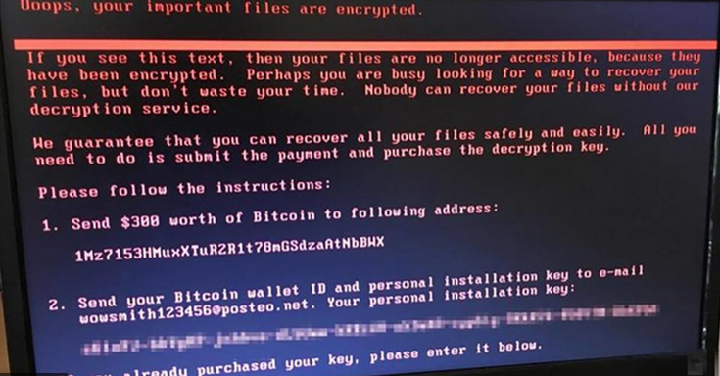
In the case of the recent cyberattacks, the virus takes the form of ransomware, malware designed to extort money.
To do this, the ransomware often uses the web or email to reach user systems.
Web-based attacks target browser, platform, or system vulnerabilities, or rely on malicious URLs or even advertisements to redirect users to sites hosting exploit kits.
Email-based ransomware, on the other hand, is typically used in targeted attacks, and relies on a variety of methods, including phishing and URLS.
Once the ransomware is activated, it allows the hacker to access the user’s computer and encrypt their personal data, preventing them from interacting with their files, applications or systems. A ransom message is then displayed on the user’s screen. It usually requires payment in virtual currency in exchange for a key to decrypt or unlock these resources.
Payment requests vary depending on the organization targeted, ranging from hundreds to millions of dollars. The message also sometimes threatens to publicly disclose compromising data if the payment request is not met.
Malware is a serious threat to global cybersecurity. As evidenced by the response to recent cyberattacks, organizations are increasingly concerned about the impact of ransomware and the monetary damage it causes while the problem is being resolved.
12 tips to protect your website and business from a cyber attack
1 – Keep your computer and software updated
Hackers look for different ways to break into a network and, usually, they can accomplish this by exploiting security holes in unedited software. Indeed, some of the software you use regularly contains vulnerabilities that can compromise the security of your computer.
However, software developers are working hard to find these errors and release updates to fix them. These newer versions contain patches to prevent malware attacks and improve the security of your system.
To ensure that you are fully protected against piracy, make sure that your applications, software and operating system are regularly updated.
It doesn’t matter which device you use, because malware can infect a variety of operating systems.
For example, Microsoft and Apple regularly release updates for their operating systems. It is strongly recommended to install them as soon as they are available.
Windows users can install them using a feature called “Windows Update”, while Mac users can use a feature called “Software Update”.
Some operating systems also offer automatic updates, so you can automatically get a new version soon after it is released.
2 – Use antivirus software and a firewall
Antivirus software can prevent malware from infecting your computer.
Of course, with antivirus software, the same principle of updating applies. Make sure you keep your antivirus software up to date, so that it blocks the latest emerging malware.
It is also necessary to protect yourself from untrusted local networks and Internet connections, either of which could give hackers and viruses a clear path to your computer.
To do this, you can use a firewall, which is a network security device that grants or denies network access to traffic flows between an untrusted area (e.g., the Internet) and a trusted area (e.g., a private or corporate network). Like a security guard at the door of a building deciding who can enter and exit, the firewall receives, inspects and makes decisions about all incoming and outgoing data.
A good firewall allows you to choose the access permissions for each program on your computer. When one of these programs tries to contact the outside world, your firewall will block the attempt and warn you, unless it recognizes the program and verifies that you have given it permission to create this type of connection.
3 – Use a non-administrator account whenever possible
Most operating systems allow you to create multiple user accounts on your computer and configure them to have different security settings.
For example, an “admin” (or “administrator”) account usually has the ability to install new software, while “limited” or “standard” accounts usually do not.
During your daily web browsing, you probably don’t need to install any new software. It is therefore recommended to use a “limited” or “standard” user account whenever possible. Doing this can help prevent malware from being installed on your computer and making changes to the overall system.
4 – Beware of emails, websites and applications
For ransomware to work, hackers must successfully download malware onto a victim computer.
The most common ways to install malware on a victim’s device are:
- Phishing emails: phishing attacks with malicious attachments or links are the primary way malware ends up on corporate networks, which means users should be wary of opening these attachments if they seem unusual. Sometimes these emails may simply be spam, but other times they may contain dangerous malware. Look carefully at the sender’s email address to see if it is from a legitimate address. Also look for obvious typos and grammatical errors in the body of the text. Hover over (but do not click on) hyperlinks in emails to see if they direct you to suspicious web pages. If an email appears to be from your bank, credit card company or Internet service provider, remember that they never ask for sensitive information like your password or social security number.
- Malicious ads on websites: in the real world, most people will be wary of walking into a dark building with an ad that is too enticing to be true. On the Internet, you should adopt a similar level of caution when entering unknown websites that claim to offer sensational things. These sites are created to spread malware and access your personal information.
- Suspicious applications and programs.
Therefore, always be careful when opening e-mails or visiting unknown websites. Remember to think twice about what you download and where you download it.
5 – Beware of pop-up windows
While browsing the web, you may encounter sites that open pop-up windows making you think your computer has been infected and asking you to download software to protect yourself.
Do not fall into the trap.
Ransomware developers often use pop-up windows offering products that supposedly remove malware. Above all, do not click on anything and close the windows safely.
6 – Create backups of your data
The greatest damage suffered by companies and individuals who are victims of malware is the loss of data, including images and documents.
Thus, the best way to protect yourself from a cyber attack is to regularly back up all your device data and website files within a completely separate system, such as a hard drive or external server without an Internet connection.
The rate at which you update your site or database will determine how often you back up. For example, if you sell online and constantly keep track of orders, you will need constant backups.
This way, you won’t lose any information if your main network is hit by a cyberattack, and you can restore your site relatively quickly and inexpensively.
7 – Strengthen passwords
Too many companies do not have strong enough password policies.
For both your personal and business accounts, and to access your website, it is extremely important to create strong passwords. A strong password contains more than 8 characters, has a mixture of upper and lower case letters and numbers and/or special characters.
You should also advise your customers who have online accounts to do the same, to protect them from future attacks.
In addition, hackers are increasingly paying attention to new ways to leverage IoT (Internet of Things) devices for malicious purposes. These devices, which include Internet-connected appliances, are often protected by default passwords. They bring a vulnerability to the network to which they are connected and make it easier for hackers to get at them.
So, don’t forget to change the default username and passwords for these devices. This step is necessary to secure your routers, printers, web cameras, DVRs and all connected smart devices.
8 – Switch your site to https with SSL
In order to securely encrypt communications between a server and a client, it is more than recommended to use the SSL (Secure Sockets Layer) protocol, if this is not already the case. This is to prevent hackers from intercepting personal data, credit card information and passwords during transmission.
9 – Protect your site by using the .htaccess file
If you are using Apache, you can protect your site from attack by simply editing your .htaccess file. Adding a few lines of instructions can block unauthorized access to the database and admin area while preventing directory browsing and file access.
10 – PCI Compliance
Payment Card Industry (PCI) compliance is a security standard that businesses must adhere to when accepting major credit cards.
This compliance ensures that your business and your customers are protected from cyber attacks and fraud by providing a basic level of security for your site. Failure to comply with the Payment Card Industry Data Security Standard (PCI DSS) can result in direct financial damages, lawsuits or government fines, and ultimately ruin a brand’s reputation in the event of a data breach.
Fortunately, it is not difficult to become PCI compliant. There are many solutions available to help you take the steps to create your own customized PCI policy.
11 – Use a vulnerability scanner
Perhaps the most famous requirement of the PCI DSS is the requirement that organizations perform internal and external network vulnerability scans at least once a quarter.
There is a reason why vulnerability scanning is required by the PCI DSS.
By detecting, locating and classifying weaknesses on an organization’s system, the Vulnerability Scanner is indeed one of the best methods to ensure that your site, applications, operating system and network are systematically protected.
The idea is to use this tool to identify and fix these weaknesses before hackers use them against you.
This scan can be performed by an organization’s IT department or provided by a security service.
12 – Use an intrusion prevention system
Since threat management can become a top priority for high-risk organizations, it is important to have a prevention and defense tool at your disposal.
This is the role of the IPS (Intrusion Prevention System), a network security technology. Unlike its predecessor, the Intrusion Detection System (IDS) – which simply monitors network traffic and suspicious activity, and alerts the administrator to malicious activity or security policy violations – the IPS detects threats and acts automatically to block suspicious activity. Specifically, the IPS can:
- Send an alarm to the administrator (as would be seen in an IDS)
- Remove malicious packages
- Blocking traffic from the source address
- Reset the connection
Because they are different, you can use a firewall or an IPS, or both, at any point on your network.









Leave a Reply
You must be logged in to post a comment.